hackaish
Test your PT skills!

This is the write-up for room hackaish on Tryhackme and it is part of our cybersecurity training from HackerU.
PURPOSE OF TESTING
The purpose of this testing was to find a vulnerability in the given system and using the vulnerability to gain privileged user access. We have to gain access to the root user.
TOOLS USED TO FIND THE SYSTEM AND VULNERABILITY
Nmap used to check at which port the application is running. msfvenom to create payload Metasploit-framework tool to find offset value,pattern-creation.
GATHERING INFORMATION OF TARGET SYSTEM AND FINDING VULNERABILITY.
We have to connect VPN to get access to the THM box.

Once VPN connected we have to deploy the machine so that we will get the target system IP

Target IP: 10.10.80.22
Now we can run a Nmap scan to find ports open and service running.

nmap -sS -sV -A 10.10.80.22
-sS (TCP SYN scan)
-sV (Version detection)
-A (Aggressive scan options)
As we can see from the Nmap scan 2 Ports were open and the service running in the port is obtained Port 22, Port 80 are open.
As Port 80 is open we will see the webpage if we find any information.

We got the username from the webpage will try to brute force ssh using hydra.

From hydra brute forcing ssh, we got a password for user ram.
username:- ram
password:- 12345
Now, will log in ssh using these credentials.

We successfully logged in using the credentials and were able to get the local.txt file.
Got our first flag submitted the flag in THM.

First flag:- e89cfe1f596f391b66c24edd6bda1a815e3de1cb
Now will try to get root access and get the root.txt file and submit our next flag.
For this first search if the user is allowed to use any application as sudo, so did sudo -l.
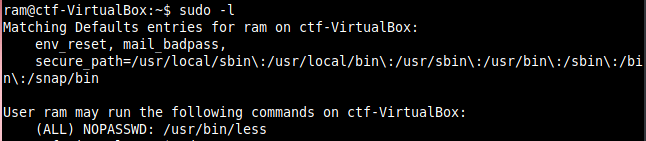
We found that less is having sudo permission so searched less in the gtfobins(https://gtfobins.github.io/#) site and found the way to get a root shell.

used the less command as shown and got the root shell.

Thus we were able to get the root shell and then went to the root directory to get the root.txt file. Successfully found the root.txt file got our second flag submitted in THM.

root flag:- cafdd99a82268e69fb00de112adf1a2b33198478
We successfully got root access to the system and got the flag, Submitted the flag in THM.








