Anthem
Exploit a Windows machine in this beginner-level challenge.

This is the write-up for room Anthem on Tryhackme and it is part of our cybersecurity training from HackerU.
Firstly we have to make a connection with VPN or use the attack box on the Tryhackme site to connect to the Tryhackme lab environment.

Now, will go through the instruction provided in the THM page for the box solving.
Instructions:-
1.This task involves you, paying attention to details and finding the ‘keys to the castle ’.
2.This room is designed for beginners, however, everyone is welcomed to try it out!
3.Enjoy the Anthem.
4.In this room, you don’t need to brute force any login page. Just your preferred browser and Remote Desktop.
5.Please give the box up to 5 minutes to boot and configure.
Now will proceed with the tasks given. Firstly we will have to start the machine to get the target system IP.

Task1:
Now will check ping with the target system before proceeding to Reconnaissance.
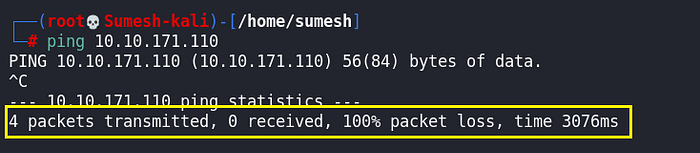
As we can see that we are not getting ping with the target the reason can be either the system is not booted yet or the system has blocked ping check.
Will confirm this using Nmap scan.

As we can see that Nmap scan didn't complete successfully and gave a message to try using -Pn in command.
nmap -sS -sV -A -Pn 10.10.171.110
-sS (TCP SYN scan)
-sV (Version detection)
-A (Aggressive scan options)
-Pn (No ping)

As we can see that adding the -Pn command we got the open ports using Nmap. Port 80 and Port 3389 are open.
We got the answer to our first three questions using Nmap scan.

Now will do further enumeration to find the remaining answers.
As Port 80 is open will search the webpage for any information we get for further enumeration.


As we searched for robots.txt we got some more information like the first line might be the password and some of the disallowed paths mentioned might we get some more information in that.
Note:- Always check for robots.txt in the website might get some information related to the disallowed or hidden directory path.
We got the answer to our next question which was to find the password from web crawler pages.

Password:- UmbracoIsTheBest!
Now will check the next question which is to find the CMS used by the website.
Which is Umbraco as it is given in the robots.txt.

Next question is to find the domain of the website which we get to know from the home page is Anthem.com

Next is to find the name of the Administrator for this will have to do little more enumeration.
We went through the two articles on the home page in one article we found a poem written.

We will copy & paste it into the search engine. As per the tryhackme hint.

From the result, we got the name of the writer might be the user name of the administrator.

We got the administrator's name, Solomon Grundy.
Since, the author of anthem blog is Jane Doe & the mail id is JD@anthem.com we can try for Solomon grundy as SG@anthem.com and the password we got from robots.txt to try login.


We got the mail address of the administrator which is SG@anthem.com.

Now we move to our next Task to find the flags.
Task 2:
For the first flag As per the hint, we have to inspect the pages.

We got two flags in the first article page source.


Flag 1:- THM{L0L_WH0_US3S_M3T4}
Flag 2:- THM{G!T_G00D}
Now will search for the third flag.
As per the hint, we have to search in the profile
By clicking on the author's name, we got flag3.


Flag 3:- THM{L0L_WH0_D15}
Now will search for the fourth flag. According to the hint, we will search the page source of the second article.


Flag 4:- THM{AN0TH3R_M3TA}
Now will move towards our next and Final Task .
Task 3:
As we already know the user name & password, let's log in with rdesktop.

rdesktop -u SG -p UmbracoIsTheBest! 10.10.171.110
Open the user file on the desktop of a user SG.We got a user flag.

user.txt content:- THM{N00T_NO0T}
For administrator’s password will have to do little enumeration.
Go to C drive. Select the option view →hidden files.

It will show u the backup file. Inside the backup folder open the restore file.
Since the restore file needs the permission
Give the full control permission for the SG user.


Open the restore file after applying the permissions.

As we got the password for the admin. We will go to the administrator user and will try to get the root flag.
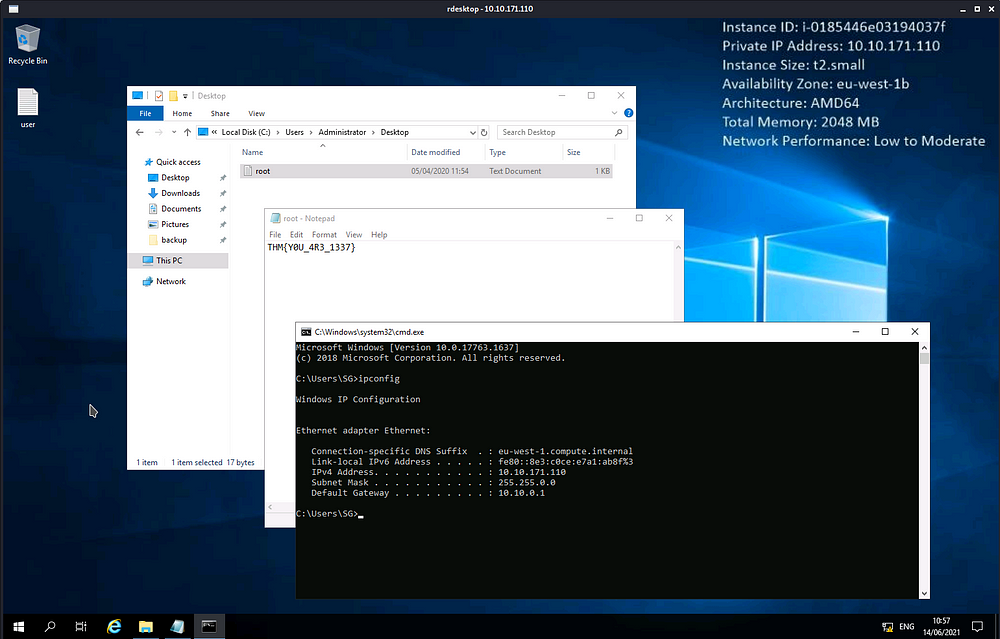

Thus we successfully able to crack the box get privilege escalation and got root access and captured the flags.